About us
In 1996, together with German and American partners such as Pro7 and computer pioneer Silicon Graphics International, we launched "Kolibri", the first German-language search engine, on the Internet.
2000 haben wir das Patent für die Fingerprinting-Technologie, das Verfahren zum interaktiven Kommunizieren zwischen einem internetfähigen Browser und einem internetfähigen Webserver, angemeldet. Auf diese Technologie basierend arbeitet wir an dem Recommandetaion Marketing der Deutschen Telekom.
In a joint venture with Bertelsmann from 2012 to 2016, a successful application for fraud prevention was realized. Earlier than others, we demonstrated the need for Self-Sovereign Identity (SSI) for data ecosystems with idento.one.
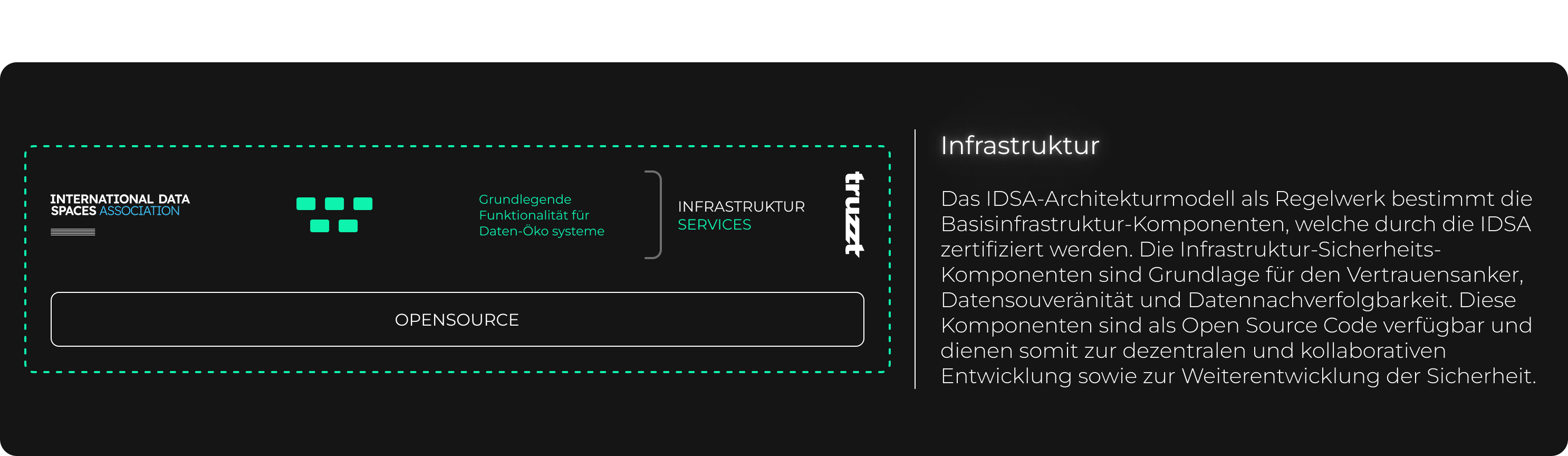
Together with Infineon and the International Data Spaces Association (IDSA), the blockchain-based application OrbiterChain was presented at the Hannover Messe and in Barcelona.
truzzt GmbH was founded in 2020. We realized that there was a great need for a solution that would facilitate the exchange of data between companies while minimizing the risks.
Together with our partners verifeye, Neuropil and GAIA-X founding partner IONOS, we are now creating a reliable infrastructure for interoperable data spaces based on European values: the truzzt box.
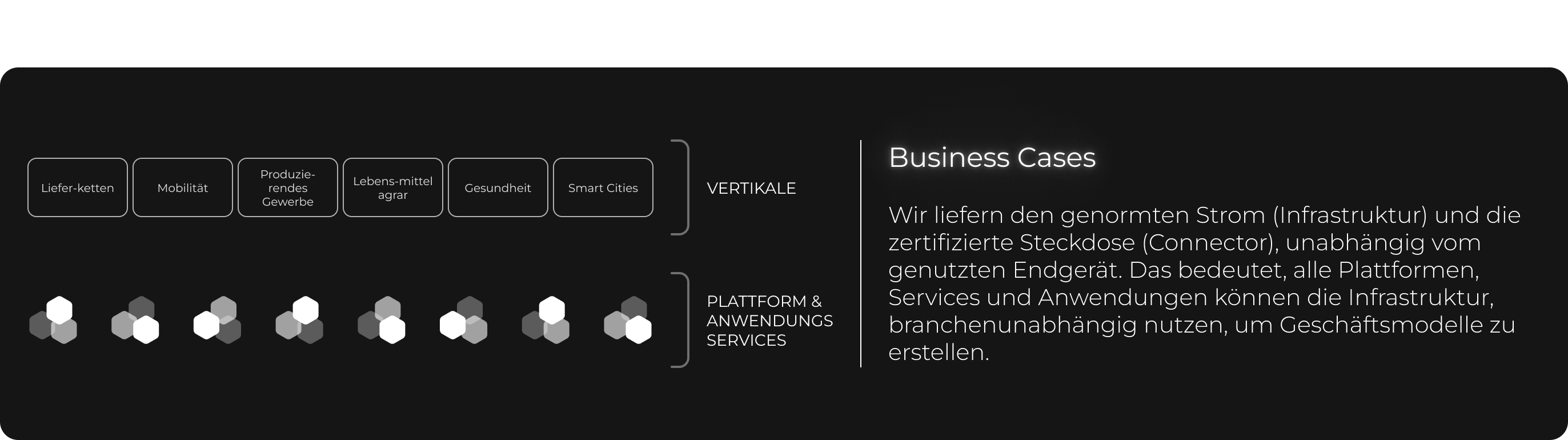
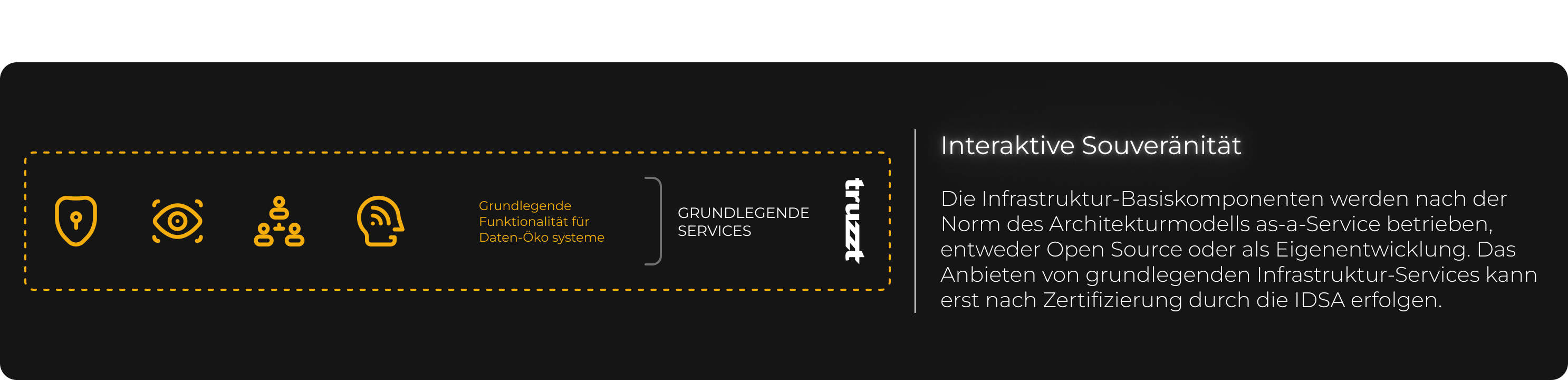
truzzt GmbH is the infrastructure provider of the IDSA reference architecture. A security gateway for the exchange of data and services using IDSA Essential Services, an infrastructure that we have played a key role in developing. truzzt thus complies with the IDSA standard DIN SPEC 27070. We are the official operator of the Mobility Data Space (MDS), a certified data space for the mobility sector based on the standards of IDSA and Gaia-X.
Our management consists of employees, some of whom have more than 30 years of experience in the Internet business. We have an experienced team of data scientists, software developers, lawyers and marketers with outstanding expertise, put together to make our vision a reality.